Book Review - 'This Is How They Tell Me the World Ends’
 Image credit: Bloomsbury Publishing
Image credit: Bloomsbury PublishingTable of Contents
Subtitle: The Cyber-Weapons Arms Race
Author: Nicole Perlroth
Published: 2021
Bottom Line
Cyber weapons have fundamentally altered our security landscape. This work provides crucial insights for anyone seeking to understand how these digital arsenals threaten civilian life.
Executive Summary
When it comes to making the shadowy zero-day market comprehensible, This Is How They Tell Me the World Ends succeeds remarkably well. Perlroth’s strength lies in revealing how cyber weapons designed for targeted operations inevitably spiral beyond their intended scope, creating cascading effects that harm ordinary civilians.
The main challenge for current cyber weapons policy is how developments have blurred the line between state-sponsored operations and civilian harm. The book’s lasting contribution is its clear-eyed examination of this critical security gap.
Review
What does it mean to weaponize software vulnerabilities? Perlroth’s investigative work explores the largely impenetrable underground cyber weapons industry with remarkable clarity. The book is accessible to non-technical readers while offering genuine insights to cybersecurity professionals.
Beginning in Kyiv, Ukraine, amidst the digital fallout of Russia’s war of aggression, the narrative travels through hacker conferences, government backchannels, and global hotspots. It demonstrates how these cyber weapons move from laboratories to real-world chaos, affecting everyone from small business owners to critical infrastructure operators.
The Author’s Credentials
Nicole Perlroth spent 13 years as a cybersecurity and cyber espionage reporter at the New York Times. Since leaving journalism in 2021, she has become a partner at Ballistic Ventures and leads her own cyber mission fund, Silver Buckshot. Her advisory roles with the Cybersecurity and Infrastructure Security Agency (CISA) and the Council on Foreign Relations further underscore her credibility in this space.
The Shadow Economy of Software Exploits
The book focuses on the global trade in so-called zero-days—exploits targeting vulnerabilities unknown to software vendors, meaning no fixes exist. Perlroth’s focus isn’t on the technical mechanics of these exploits. Her interest lies in the moral, political, and societal implications.
Unfortunately, the reality is that governments, brokers, and mercenaries compete to buy and stockpile cyber weapons in a shadow market. These are deployed to attack power grids, nuclear facilities, hospitals, and civilian systems. The use of such weapons often blurs the line between espionage and sabotage.
This blurring becomes starkly evident in her account of the NSA’s offensive capabilities and how stolen USA cyber weapons were reused by the Russian military. This becomes a case study in how malicious software, once released, can boomerang back to harm its creators.
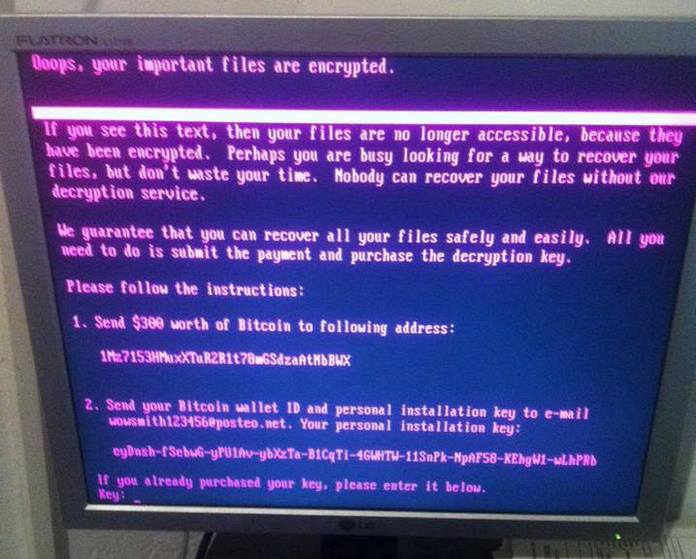
A ransom note from the NotPetya ransomware. The US Department of Justice has charged six Russian GRU Unit 74455 officers for this attack, which used stolen NSA exploits. Source: uain.press
The Human Cost
The book also excels by bringing a global lens while rooting the narrative in everyday experiences. In Ukraine, a woman loses her small knitting business when the postal service goes offline. A man is turned away from a car purchase when registration systems crash. The cascade effects of offensive cyber operations are not abstract concepts, they’re felt in daily life by ordinary people.
The zero-day market, she argues, is not just a matter of national security but a fundamental risk to civilian life. What stands out is the sense of inevitability she conveys, that the very architecture of the internet, coupled with short-sighted policy, has created a threat surface no one can control.
Strengths and Limitations
One of Perlroth’s considerable strengths is her access to top hackers, cyber mercenaries, and government insiders. The tone is urgent but not alarmist, and the book manages to be readable, serious, and nuanced simultaneously.
However, there are some weaknesses in the framing. One main challenge with the term ‘cyberwar’ as used in the book is that it stretches the concept too far. When it comes to actual warfare, we don’t yet see cyber operations delivering the kinetic or political transformation we associate with traditional military conflict. Not in isolation, at least.
Additionally, while Russia and the USA receive extensive treatment, the book gives relatively less space to Chinese state-sponsored hacking operations.
Current Relevance
Since the book’s release in 2021, the cyber landscape has evolved rapidly. Ransomware has become heavily industrialized, and artificial intelligence is beginning to reshape attack surfaces and defense strategies alike. Both the EU and USA have explored defining exploits as cyber weapons subject to export controls, though with mixed results.
Conclusion
Perlroth’s central argument, that cyber weapons can escape their handlers and that we’re woefully unprepared for the consequences, remains alarmingly relevant.
The most important insight given by the book is that cyber weapons policy affects everyone, not just governments and military organizations. Whether you’re a cybersecurity professional, policy maker, or concerned citizen, this work provides crucial understanding of how digital arsenals threaten civilian life.